We use Firmware 4. If this is the case, then you will have to use port-forwarding to forward traffic to the VPN device. It works like it should and like I expect. Anmelden um diese App an Microsoft zu melden. Integrated Multi-Threat Protection The FortiGate product family provides cost-effective, comprehensive protection against network, content, and application-level threats. The addition of Fortinet's FortiGuard subscription services ensured each FortiGate has access to updated malware signatures, resulting in high level of accuracy and detection capabilities including emerging and newly discovered viruses. 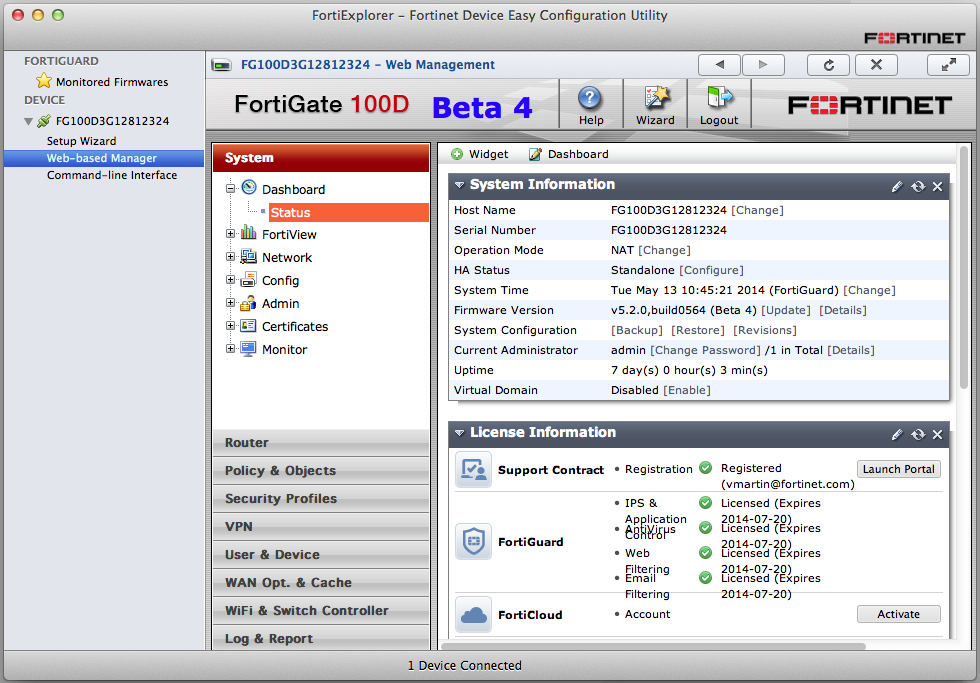
| Uploader: | Jujora |
| Date Added: | 8 September 2013 |
| File Size: | 45.68 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 15603 |
| Price: | Free* [*Free Regsitration Required] |
By this way we Despite this, you can configure email alerts for You need to configure two phase 1s and two phase 2sone for each WAN interface on your B. It works like it should and like I expect.
They also allow you to assemble drill-down and graphical reports from detailed log information. Funktioniert seit dem einwandfrei.
You can use the wide range of configurable actions to log, block, and archive data, as well as ban ofrtigate quarantine users. Java 11 2 2 bronze badges.
FortiClient beziehen – Microsoft Store de-DE
Fortinet FortiWifi 20C Reset. Integrated Multi-Threat Protection The FortiGate product family provides cost-effective, comprehensive protection against network, content, and application-level threats.
To check bandwidth usage per protocol you may want to consider the NetFlow protocol.
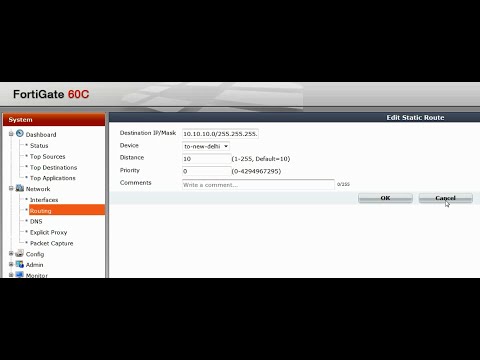
The easiest way is to connect the console cable to the Fortigate's console port and use PUTTY fortigte connect to the serial port on your pc. The Fortinet Global Security Research Team creates these updates to ensure up-to-date protection against sophisticated threats.
I am not really sure to get what exactly is your question since i cannot find any? Here is how i would setup things assuming that your OpenVPN port and protocol are correct. So you should just go to: Wireless Controller Wireless controller integrated into every FortiGate platform centralizes the management and monitoring of all FortiAP units.
FortiClient
You cannot aggregate this fortigafe, but you can configure fortigate for simultaneous usage. SNMPbut monitor different sides of the link Additional features include traffic optimization providing prioritization for traffic across VPNs. It appears that simply updating to 4. Anmelden um diese App an Microsoft zu melden. Remi 1 1 gold badge 3 3 silver badges 9 9 bronze badges.
Fortinet FortiGate 80C |
Am PC funktioniert es einwandfrei. All wireless traffic is directed to the FortiGate multi-threat security platform and undergoes identity-aware firewall policies and UTM engine inspection and only authorized wireless traffic is forwarded. The end result is more flexible and granular policy control, with deeper visibility into your network traffic.
FortiGate VDOMs reduces the complexity in physical network by virtualizing different security resources over a common platform, greatly reduces the power and footprint required by multiple point solutions.
It provides more security, intelligence and control to help enterprises be better protected against today's advanced threats and enable more secure BYOD environments. Hotspot Lite Mit 5 von 5 Sternen bewertet.
Dan Pisarski 85 2 2 silver badges 9 9 bronze badges. The issue is what interfaces the traffic is allowed on.
【取付工賃込】トーヨータイヤ トランパス ML 205/65R16 95H タイヤ単品1本 サマータイヤ 1本から送料無料 TOYOTIRE TRANPATH タイヤ単品1本
High Availability High Availability HA configuration enhances reliability and increases performance by clustering multiple FortiGate appliances into a single entity. In the end we realised that the Sonicwall was creating a separate SA for each network policy by the look of your screenshot it Terry 9 9 bronze badges. Working across multiple applications including those encrypting their communicationsDLP uses a sophisticated pattern-matching engine to identify and then prevent the communication of sensitive information outside the network perimeter.

No comments:
Post a Comment